Configure Entra ID as Cloud Director IdP
Cloud Director organizations can use local accounts for administration. But larger organizations may already have some sort of identity provider in place such as Microsoft Entra ID. So why create and manage local users when you already have an IdP available?
This article describes the configuration steps for using Microsoft Entra ID as an identity provider for Cloud Director.
Prepare Cloud Director
The first step is logging in to Cloud Director with a local account that has Organization Administrator rights. Go to the Administration menu and click on SAML in the Identity Providers section.
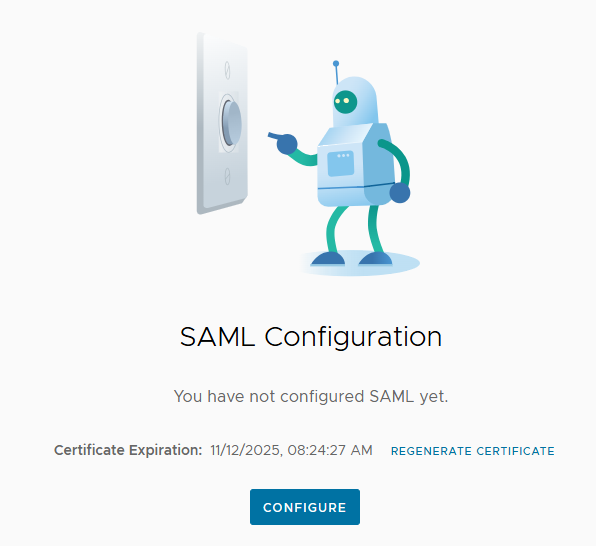
Click on the Configure button.
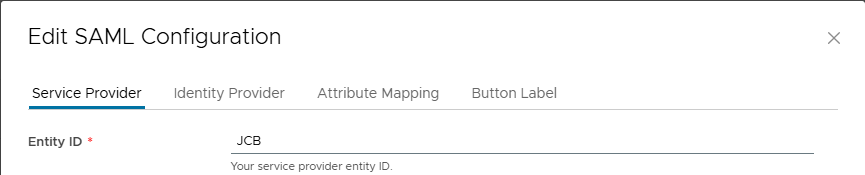
Enter an Entity ID for the system organization. The Entity ID uniquely identifies your system organization to your Identity Provider. DO NOT USE SPACES. Click on the link Retrieve Metadata. Make a note on the location of the saved file. You will need it later on.
Click on the Identity Provider tab and enable Use SAML Identity Provider.
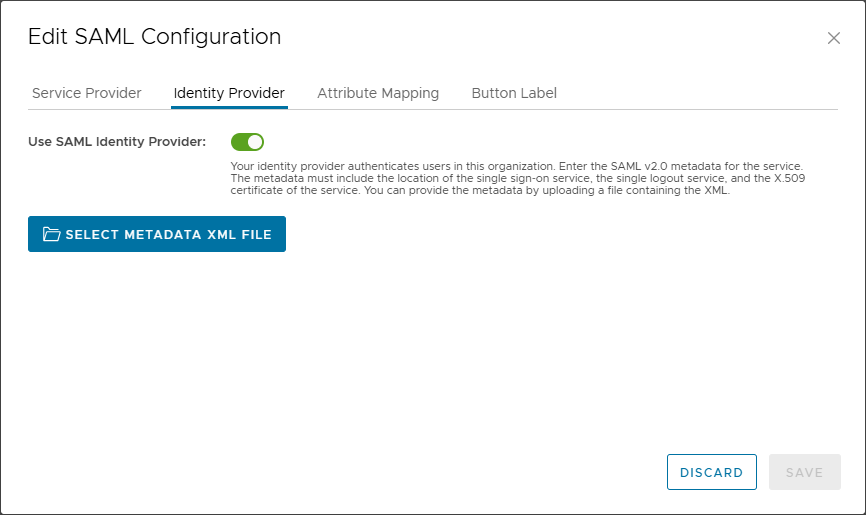
For the next step we need a metadata XML file from Entra ID. So lets create an application for that.
Create Entra ID Application
Login in to the Azure portal and open Microsoft Entra ID. Click on Manage, Enterprise Applications and click on New application.
Next click on Create your own application.

Give the application a name and select the option Integrate any other application you don’t find in the gallery. Then click Create.
The Azure portal opens the application and gives you some steps to take. Here you can add users and or groups to the application. Then select Manage, Single sign-on.
Click on SAML.
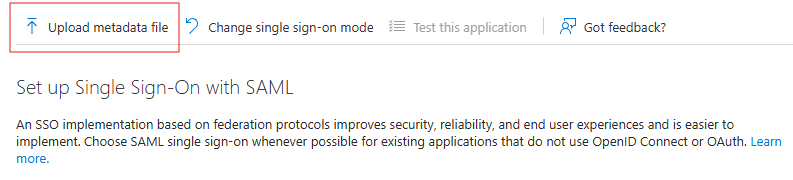
The next step is to upload the metadata file you downloaded with Retrieve Metadata link in Cloud Director. Click on Upload metadata file and select the file.
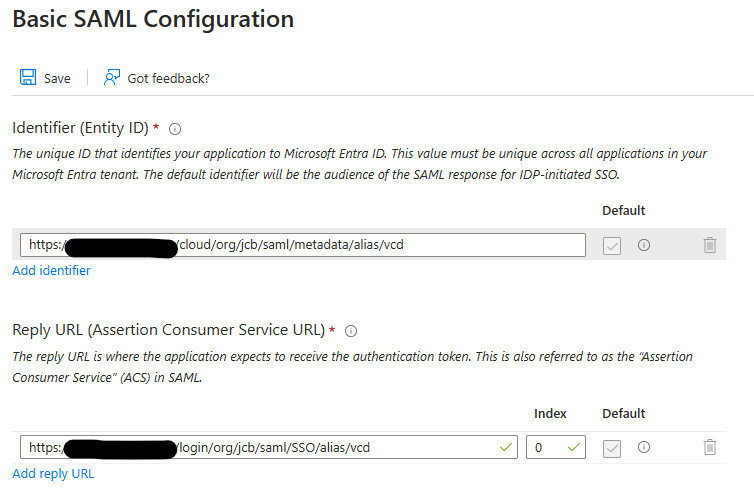
In the previous picture you see that the default identifier is different than the identifier you entered in Cloud Director. There we used “JCB“ as the Entity ID. To add this identifier click on Add identifier and type the same identifier you typed in Cloud Director. Or you can change the current identifier. As long as the name used in Cloud Director exists.
Now you have to download the Federation Metadata XML file from the Azure portal. Under 3 SAML Certificates click on the download link. Remember the name and location of the downloaded file.
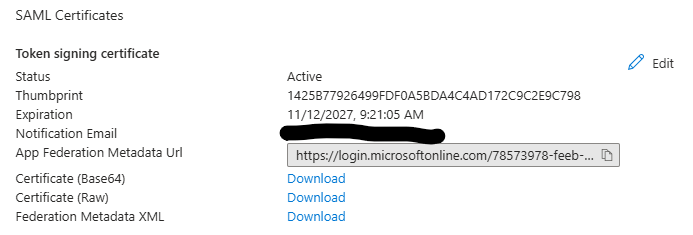
Return to Cloud Director and click on Select Metadata XML File.
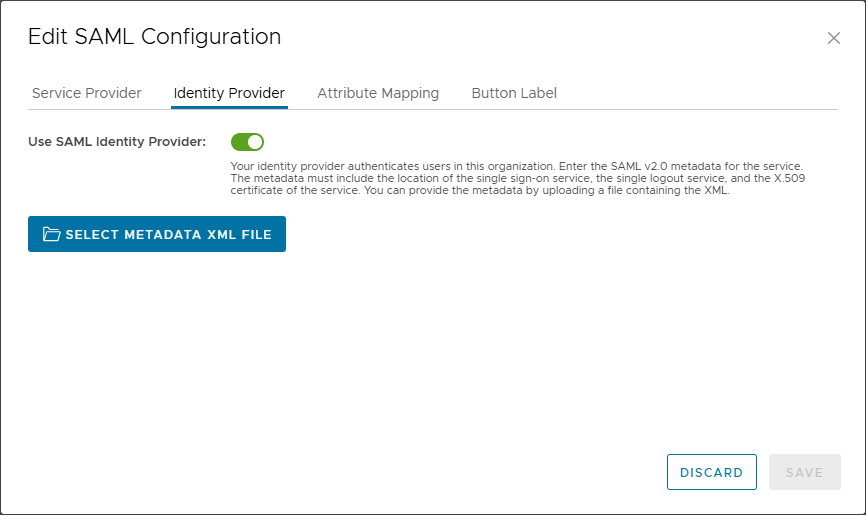
Browse to the file you downloaded from Azure and save the configuration. The next step is to import users and/or groups in Cloud Director.
Import Users
Go to Access control and click on Users.
Then click on Import Users.
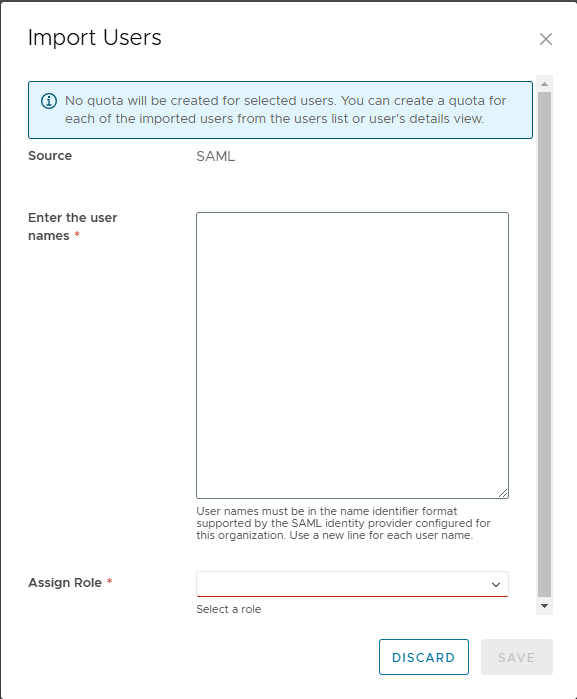
Enter the user names, select the role and click on save.
Import groups
If you want to use groups you must add a group claim for your application in Entra ID. Open the application and choose single sign-on. Then click on the Edit link for Attributes & Claims.
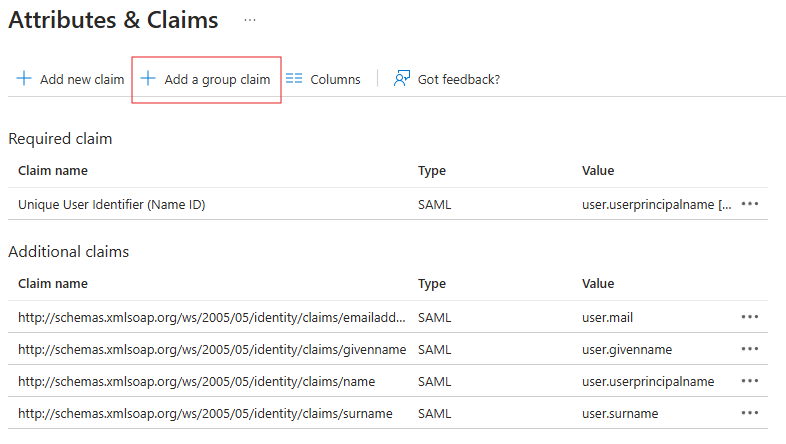
Click on Add a group claim.
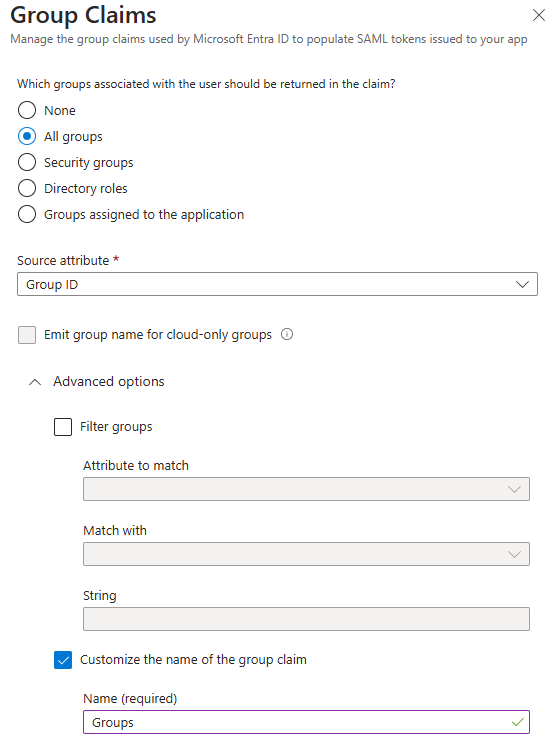
Select All groups and under the Advanced options enable Customize the name of the group claim. Enter Groups for the name. This is important, otherwise it won’t work. Click on Save.
Now return to Cloud Director.
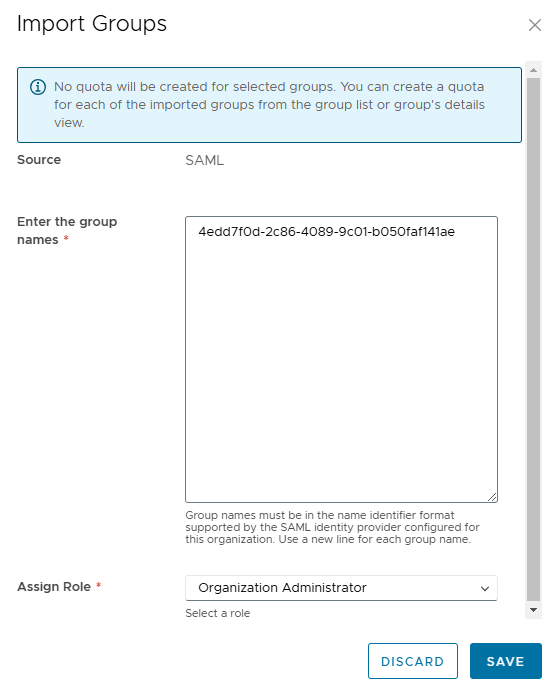
Go to Access Control and click on Groups. Then click Import Groups.
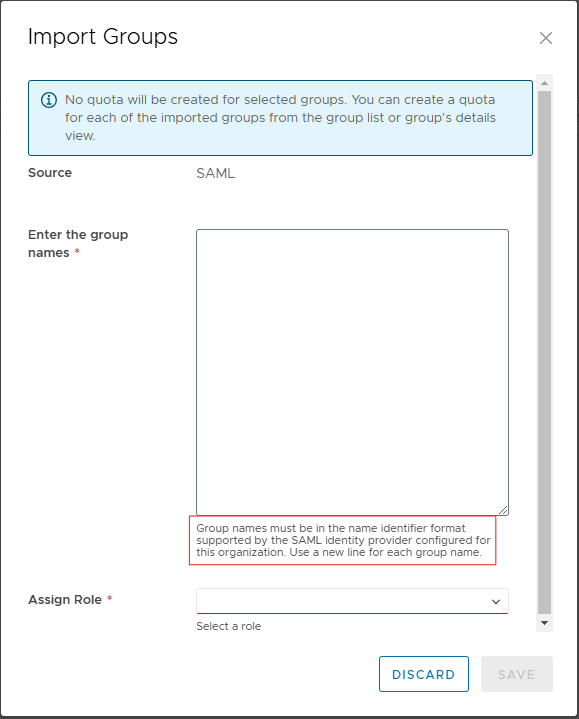
Enter the name of the group you want to import and assign the role. Then click on save.
For Entra ID the name of the group that is returned as a claim is the object id of the group. So use that id for the name. Here is an example: